
Microsoft Threat Modeling Tool For Mac
Thanks for downloading the Azure SDK for Mac. This page provides resources to help you get started using the Azure SDK for node.js, PHP, or Python. To get started with node.js applications on Azure: Install node.js by using the node.js Macintosh installer. Install git on your Mac using the git Mac OS X installer. Microsoft Defender ATP for Mac does not depend on any vendor-specific features. It can be used with any MDM solution that supports the following features: Deploy a macOS.pkg to managed machines. Deploy macOS system configuration profiles to managed machines. Run an arbitrary admin-configured tool/script on managed machines.
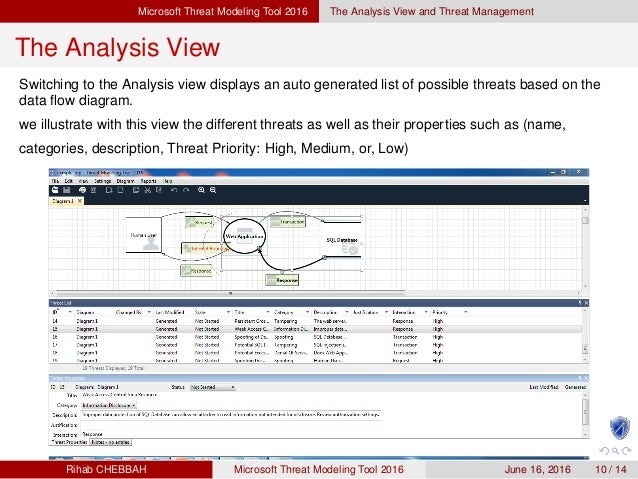
The Threat Modeling Tool is a core element of the Microsoft Security Development Lifecycle (SDL). It allows software architects to identify and mitigate potential security issues early, when they are relatively easy and cost-effective to resolve. As a result, it greatly reduces the total cost of development. Also, we designed the tool with non-security experts in mind, making threat modeling easier for all developers by providing clear guidance on creating and analyzing threat models.
The tool enables anyone to:
- Communicate about the security design of their systems
- Analyze those designs for potential security issues using a proven methodology
- Suggest and manage mitigations for security issues
Here are some tooling capabilities and innovations, just to name a few:
- Automation: Guidance and feedback in drawing a model
- STRIDE per Element: Guided analysis of threats and mitigations
- Reporting: Security activities and testing in the verification phase
- Unique Methodology: Enables users to better visualize and understand threats
- Designed for Developers and Centered on Software: many approaches are centered on assets or attackers. We are centered on software. We build on activities that all software developers and architects are familiar with -- such as drawing pictures for their software architecture
- Focused on Design Analysis: The term 'threat modeling' can refer to either a requirements or a design analysis technique. Sometimes, it refers to a complex blend of the two. The Microsoft SDL approach to threat modeling is a focused design analysis technique
Next steps
The table below contains important links to get you started with the Threat Modeling Tool:
| Step | Description |
|---|---|
| 1 | Download the Threat Modeling Tool |
| 2 | Read Our getting started guide |
| 3 | Get familiar with the features |
| 4 | Learn about generated threat categories |
| 5 | Find mitigations to generated threats |
Resources
Zyxel g-202 driver. Here are a few older articles still relevant to threat modeling today:
Is there a better alternative?Yes. Betternet claims to never use any of your personal details, but it does track your network information, unique device ID and operating software. Where can you run this program?Betternet can be run on Windows, macOS and Linux desktops. The program says this is simply for trouble-shooting and marketing purposes, but by launching the app you can give away your location and device details. On mobile browsers, it can be run on iOS, Android, Windows and BlackBerry. 
Check out what a few Threat Modeling Tool experts have done: